Deployment of Network Security Devices
Overview
Everyday, new viruses, worms and software security vulnerabilities of all types are discovered on the Internet. Network security is becoming an ongoing network monitoring and management activity. In response to these security hazards, the Computing Services Centre (CSC) is continuously making use of the most advanced technologies and security management devices to protect the campus network.
This article depicts current technologies and security devices that are deployed by the CSC. The objective of such effort is to provide Internet Access to all campus users with the following benefits:
-
Safe and Stable Internet Environment
-
Fast Access and Quick Application Response Time
- Fairness in sharing Internet bandwidth
In addition, we are not only protecting the attacks originated from the Internet. Our deployment also caters for the detection and protection of attacks generated from internal users.
Types of Security Devices
In order to achieve the above objectives, a number of security devices are deployed between the campus backbone and the Internet. These devices can be divided into three categories:
-
Internet Router and Firewall
Internet Router and Firewall enforce the network policy and permit only allowed traffic/protocol with the correct IP address range under the correct state to pass through. The policies are rather static and the packet examination is performed by some specific hardware. It provides a fast filtering mechanism to reject all packets that violate the network policy. -
Intrusion Protection System (IPS)
Even network packets that are allowed to pass through firewall may contain virus. For example, all email traffic must be allowed to pass through the firewall as indicated in our firewall policy. In this regard, the IPS provides a second level of network packet examination based on its knowledge of attack signatures, normalized traffic pattern and behavior. To put it simply, the IPS is like an "Anti-Virus" software running in a network appliance to examine the network packets at multi-gigabit level. For details about the IPS deployment in CityU, please visit: http://www.ncm2.xyz/csc/netcomp/sep2004-5.htm -
Traffic Shaping Device
With numerous network applications running across our campus network at the same time, these applications all struggle for the Internet Bandwidth. How can we allocate the Internet bandwidth to satisfy the academic needs but in a fair and appropriate way?
Traffic shaping device helps us to make a fair allocation. Packet shaping device can automatically learn and classify network traffic flowing inline across it. In addition to blocking and permitting network packets, traffic shaping device can also increase, shape and provide guaranteed bandwidth for some pre-defined applications. The following traffic parameters are used to shape network traffic:
With the advance of traffic shaping technologies, the above shaping policy can be applied to each application generated from a specific IP address. This prevents one host from dominating in certain application and using up all the provided bandwidth. In addition, the real time alert and reports generated by packet shaping device clearly show how the Internet bandwidth and connections are being allocated/consumed. The figure below demonstrates how the report provides such variable network information to the administrator.
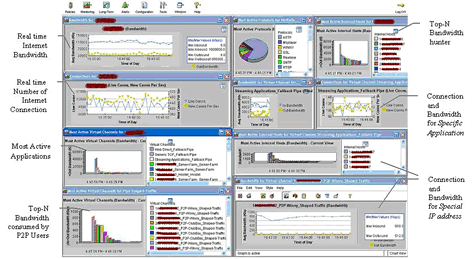
Figure 1 Real Time Traffic Statistics generated by Traffic Shaper Device
Besides just blocking or permitting certain IP addresses and applications, network administrators can now have a better understanding of the application characteristics; the bandwidth, connection and time/latency requirements based on the above live statistics. This enables us to derive a shaping policy that can allocate appropriate bandwidth, connections to users and applications and satisfy the actual and real time needs of the University.
At the same time, some non-critical applications can still enjoy the remaining network bandwidth that would otherwise be wasted. This achieves the objective of providing a fast access and quick response time in a prioritized, fair and scientific manner.
Roles of Internet Security Devices
With the deployment of the above security management devices, many of the network attacks are blocked. The table below summarises the functions and roles of the network security devices deployed in the campus.
|
Attacks Category
|
Protected by
|
| IP address spoofing | Router, Firewall |
| Port Scanning | Firewall, IPS |
| Protocol Anomaly | Firewall, IPS, Packet Shaper |
| Message Spamming | IPS |
| Brute Force Login Attempt | IPS |
| BackDoor/IRC Bot Attacks | IPS, Packet Shaper |
| P2P Software | IPS, Packet Shaper |
| Vulnerability Attack | IPS |
| Application Server Attacks/Injection | IPS |
| Email Virus/Worm | IPS |
| DOS/DDOS Attacks | IPS, Packet Shaper |
| Priority, Bandwidth, Connection Shaping | Packet Shaper |
|
Table 1 Roles of Network Devices in Security Protection |
All of the above devices have been evaluated and tested carefully before deployment. The following are the major criteria for evaluation and deployment:
-
Stability and reliability
-
Processing power
-
Accuracy in traffic classification
-
Latency
-
Number of False Alarm/Positive
-
Granularity of the policy/configuration setting
-
Provision of Real Time and Historical Statistics
-
Frequency and Response in the update of Attack Signature
-
Product Maturity and Development Status
After a series of testing and fine-tuning of the network security devices, we have now strengthened the protection against various types of network attacks originated from both the Internet and internal users. In addition, the real time and historical reports clearly show how the Internet bandwidth is being used, thus providing solid information as a source for attacks forensic analysis and network policy refinement.
Currently, we have successfully blocked thousands of attacks to the University every day. Besides blocking attacks, we can also differentiate among many network applications, thus allowing us to provide better network resource to some pre-defined applications.
Furthermore, with the adoption of network security devices in the Internet Gateway of CityU, we can achieve our objectives of providing a stable, safe, fast, responsive and fair Internet access to all campus users.