I. Background of Code Injection
/* The following article is extracted from the "Information Security Newsletter" published by the JUCC IS Task Force. */
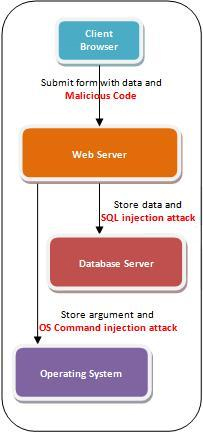
Code Injection is a type of exploitation caused by processing invalid data input. The concept of injection attacks is to introduce (or "inject") malicious code into a program so as to change the course of execution. Such an attack may be performed by adding strings of malicious characters into data values in the form or argument values in the URL. Injection attacks generally take advantages of inadequate validation over input/output data, for example:
- Lack of defining a class of allowed characters (such as standard regular expressions or custom classes)
- Lack of restricting the data format (such as date format yyyy/mm/dd)
- Lack of checking the amount of expected data (such as maximum length restriction)
- Lack of restricting the data type (such as numerical input only)
- Web Level
- Application/Database Level
- Operating System (OS) Level
- Web Level
Today, most websites embed dynamic contents in their web pages for better user experience and functionalities. Dynamic content is generated by the respective server process, which can behave and display differently according to users' settings and requirements when delivered. Dynamic websites are more vulnerable to a type of code injection, called Cross-Site Scripting ("XSS"), than those traditional static websites.
In this form of injection attack, the attackers introduce improper scripts into the web browsers. The technique is most often used to inject JavaScript, VBScript, ActiveX, HTML, Flash or any other types of codes that web browsers may execute. Once the injection is successfully performed, hackers can carry out a variety of malicious attacks including account hijacking, changing of user settings, cookie theft and poisoning, or false advertising.
Reference:
http://www.owasp.org/index.php/Code_Injection
http://www.cgisecurity.com/xss-faq.html#whatis
http://www.ibm.com/developerworks/tivoli/library/s-csscript/
-
Application / Database Level
Nowadays, deploying web applications is a popular mean to enable users to easily search for specific data on the Internet or intranet. For example, a university may create a web portal that allows its students to search their course information and academic records.
Web application injection attack aims at exploiting a website through entering improper user-supplied data. Such attacks usually involve injection of malicious commands via the input data submitted by the client, which is later passed to the server to affect the execution of predefined queries.
A successful web application injection exploit can read sensitive data from the database, modify database data, and execute administrative operations within the database (e.g. shutdown the database management system (DBMS)). Two common injection techniques, SQL injection and LDAP injection, both fall into this category.
-
OS Level
Some shell applications would base on the user-supplied inputs to select which program to run, which commands to use as well as which arguments for the program. Any web interface that does not properly sanitise the input is vulnerable to this exploit.
With the ability to execute OS commands, the attackers can inject unexpected and dangerous commands, upload malicious programs or even obtain passwords directly from the operating system. The problem would be even worse if the compromised process fails to follow the principle of least privilege, which allows the attacker's commands to be executed with special system privileges that increase the amount of damage.
Reference:
http://msdn.microsoft.com/en-us/library/ms161953.aspx
http://blogs.sans.org/appsecstreetfighter/2010/02/24/top-25-series-rank-9-os-command-injection/
http://cwe.mitre.org/data/definitions/78.html